Hackers Have Found a New Incentive to Target Shipping
The biggest shipping casualties can move markets, and the hacking community has noticed

The commercial maritime industry operates over 90,000 vessels across various segments, from merchant ships to offshore support vessels. Developments in digitization, automation and smart tech have increased the efficiency of marine operations, transforming processes that were previously conducted manually.
However, these developments have also created new cyber challenges, like outdated and unsupported software, intrusion into vessel systems and crew-related factors. Many onboard OT systems were installed during vessels’ original construction, as long as 25-30 years ago. With such long lifespans, many commercial vessels are now running outdated and unsupported software, including within operating systems. This makes it easy for attackers to identify ways to target them.
In particular, malicious intrusion into vessel control and OT equipment is an inherent risk with severe implications. One of the worst-case scenarios could be that attackers could cause loss of navigational control. Crews often rotate, which means that they use systems they are unfamiliar with. Given the above vulnerabilities, severe and effective attacks could be on the way.
A recent example of severe disruption to the maritime transportation system was the Suez Canal incident in March 2021. At the center was the Ever Given, a 220,000-ton, quarter-mile long container ship. Strong winds blew it off track while entering Egypt’s Suez Canal, where 12 percent of the world’s seaborne trade passes each year. The ship completely blocked the waterway, causing disruptions and delays.
The incident was not a cyberattack, but it demonstrated to potential attackers how one grounding on a globally significant shipping route could have wider implications to global trade and stock markets. This unveiled a new incentive for targeting vessels.
An opportunity arose for attackers, evidenced by discussion on the dark web. The incident's global impact was vast, especially on stock markets. Vessels containing a wide variety of trade commodities were delayed (Figure 1). Many top European industries were impacted, including construction, wholesale trade and health services. For example, machinery company Caterpillar considered airlifting parts to overcome the blockage.
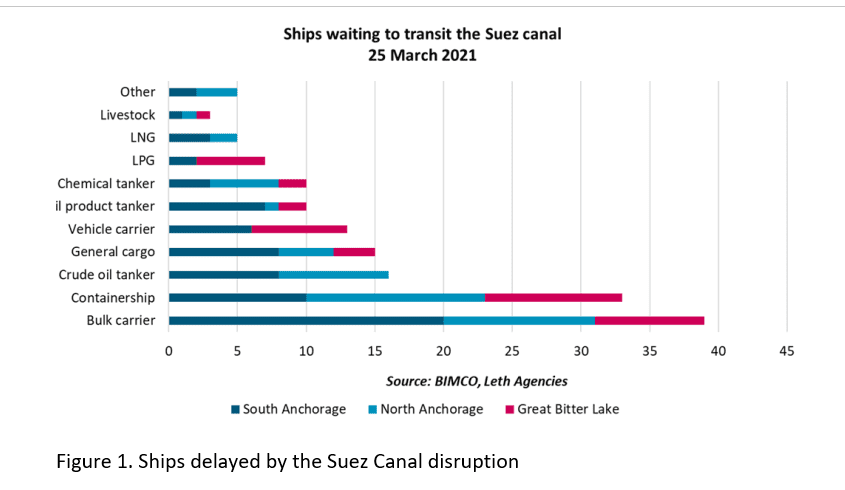
Delays resulted in losses. Supply chain disruptions can cause major price dislocations, which can impact prices on financial markets. The blockage held up an estimated $400 million an hour in trade, based on shipments that were on the affected vessels in and around the Suez Canal.
Having seen the vast impact on the stock market, attackers realized they could purchase certain stock before committing an attack and profit from it, with knowledge of the upcoming attack. They could invest in certain commodities and avoid being tracked as they might with ransomware requests. Attackers could use viruses tested onshore to target vessels’ systems.
Hackers have been using their skills to make illicit gains on the stock market for many years, especially since 2015. Over a five-year period, up to 32 stock traders and hackers infiltrated computer servers of PRNewswire Association LLC, Marketwired and Business Wire, a unit of Warren Buffett's Berkshire Hathaway Inc. They used early access to 150,000 news releases on mergers, acquisitions and financial results to trade prior to information becoming public. Five of these traders were arrested in Georgia and Pennsylvania while four others remain at large.
Commercial vessels are the pillars of international trade. Their critical role in the stability of markets makes them increasingly vulnerable to this novel type of attack. This new threat has wide implications for maritime, making implementation of cyber security measures even more important.
Jessie Hamill-Stewart is a cybersecurity PhD student at University of Bristol and University of Bath.

that matters most
Get the latest maritime news delivered to your inbox daily.
Dr. Dmitry Mikhaylov is CSO and Co-Founder of Reperion.
Andrew Sallay is the CEO and co-founder of cybersecurity company Reperion.
The opinions expressed herein are the author's and not necessarily those of The Maritime Executive.
