Cybercriminals Hit Naval Shipyard Austal USA
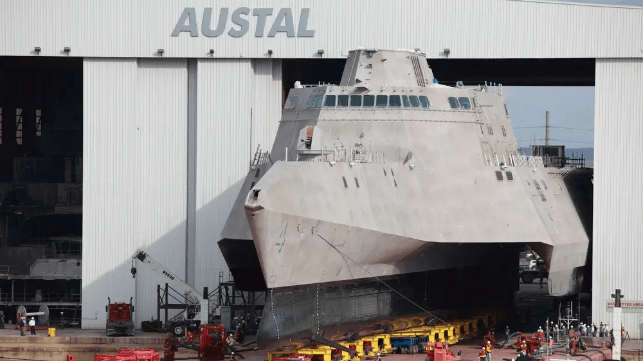
Australian-owned defense shipbuilder Austal USA has had an up-and-down year, and has already had to contend with a criminal prosecution, a money-losing tug bid, and turnover in the C-suite. This week, the cyber threat group Hunters International claimed that it hacked Austal and stole unspecified data; the shipyard holds multiple U.S. Navy orders, including a supply contract to build section modules for new nuclear submarines.
In a list of new victims posted on its Dark Web site over the weekend, Hunters International said that it has data from Austal's U.S. operation and will release up to 43 samples soon (below).
New victim claims on the threat group's online dashboard (Hunters International)
It is Austal's second run-in with hackers since 2018, and it comes at a sensitive moment. The firm is said to be in talks with three different investors about a potential sale, according to the Financial Review.
In a statement Wednesday, Austal USA said that it was aware of the breach and that no classified data or personal data had been stolen. The cyberattack had no impact on operations, Austal said, and the FBI and NCIS are investigating.
"Austal USA recognizes the seriousness of this event and the special responsibility we have as a DoD and DHS contractor. Our assessment is on-going as we seek to fully understand this incident so that we can prevent a similar occurrence," the firm said in a statement. "Regulatory authorities, including the Federal Bureau of Investigation (FBI) and Naval Criminal Investigative Service (NCIS) were promptly informed and remain involved in investigating the cause of the situation and the extent of information that was accessed."
Most commercial cyberattackers use malware to encrypt victims' files, then demand a ransom in exchange for the decryption key. Hunters International is of a different breed. The group focuses on stealing data, then using it to blackmail or pressure the victim. It is not afraid of causing collateral damage in order to get paid: earlier this year, the group hacked a Beverly Hills plastic surgery clinic and released confidential photos of several patients - and noted that it had another 250,000 files from the same business.
Its malware appears to descend from code used by the now-defunct Hive group, according to security researchers. Hive, a notorious malware organization with more than 1,300 victims and $100 million in ransom payouts, was disrupted and disbanded by law enforcement earlier this year. In a statement in October, Hunters International denied a direct connection with Hive, and said that it had only bought Hive's code and improved upon it.
